
16 November, 2023
Analyzing the security of WordPress from a historical perspective
Over the last two decades, web content management systems such as WordPress have emerged as a versatile and transformative tool. This article, written by security consultant Emil Kylander Edwartz, takes a comprehensive look at WordPress with a specific focus on its role and security within the Swedish context.
WordPress (WP) is a web content management system (CMS). It was initially created to publish blogs, but has now evolved to power a wide spectrum of websites, including e-commerce, forums, traditional websites and image galleries. Today, WordPress is one of the most popular CMS, powering 43.1 % of all websites as of 2023 according to W3Techs.
How secure is Wordpress?
WordPress’ internal security team as well as and external security analysts regularly audit the platform’s core due to how widely adopted the software is. However, threat actors also search for vulnerabilities on this platform – either for personal gain or by selling zero-day exploits for hundreds of thousands of dollars to zero-day brokers. The current price for a Remote Code Execution vulnerability on one zero-day vendor is $300,000-$500,000 USD, but it can also exceed that amount.
CVEDetails is a good resource for examining vulnerabilities existing in various software updates. As of november 2023, there are 349 vulnerabilities in the Wordpress core. In total, there has been five vulnerabilities reported, all of them are medium severity as can be seen here. Between 2006 and 2021, there has been 27 critical vulnerabilities on different WordPress versions.
Because of WordPress' rich features, uploading plugins or editing files from the administrator panel is possible. Attackers can abuse this feature if a cross-site scripting vulnerability (XSS) exists. Back in 2014, the CVE number CVE-2014-9031 was published. This was a cross-site-scripting vulnerability in the WordPress comment section. Attackers utilized this by automatically submitting comments with a JavasScript payload to various WordPress websites. When administrators moderated their comments, the JavasScript payload was executed in the session of the administrator account and automatically uploaded a malicious PHP plugin that let an attacker compromise the website. This is also known as a Blind Cross-Site-Scripting (XSS)
How good are Swedish system administrators at keeping their WordPress sites updated?
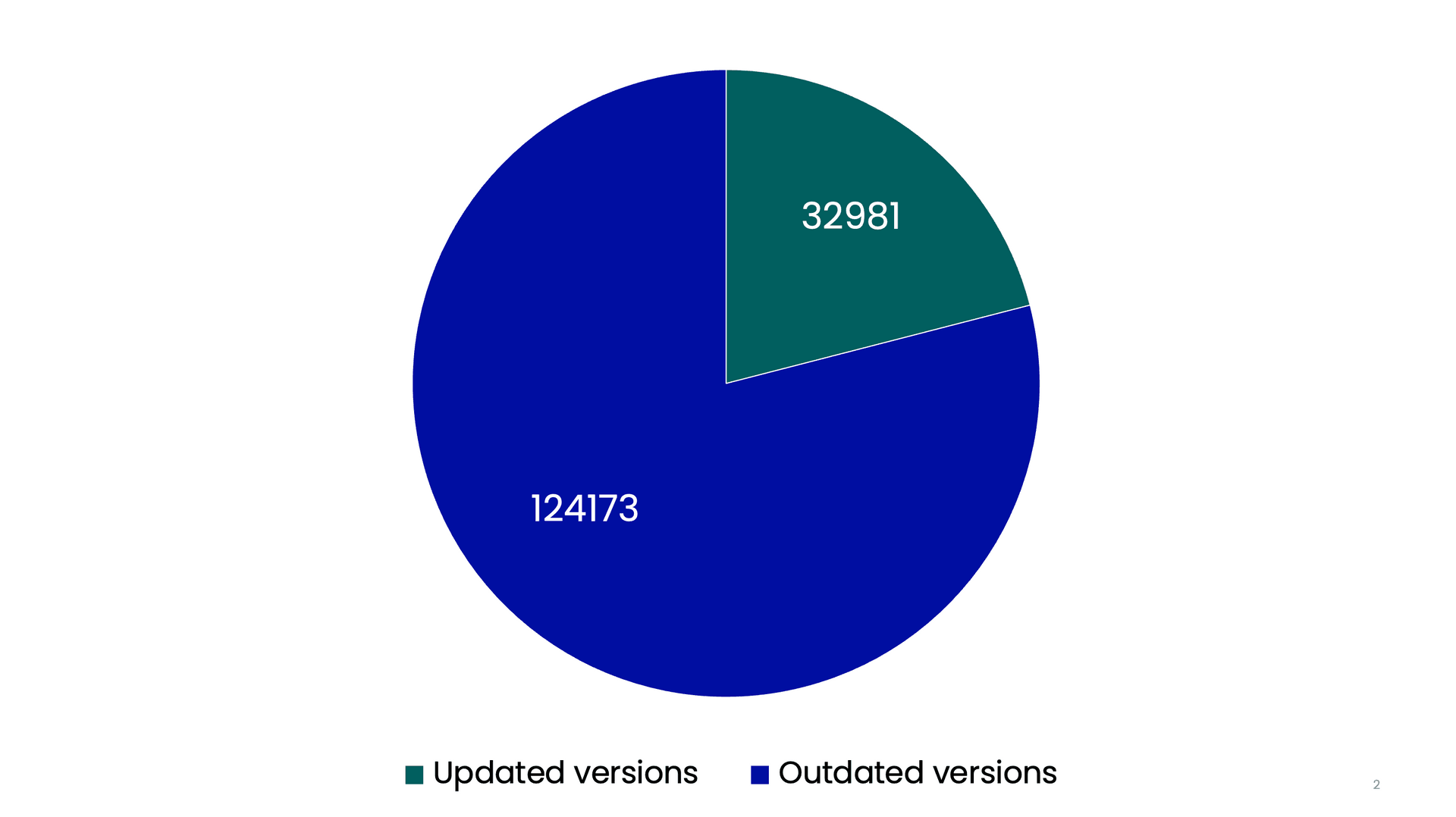
To come up with an answer to this question, Emil Kylander Edwartz has scanned 700,000 Swedish websites. In total, 240,939 websites were identified to be WordPress from analyzing the HTML code – putting the percentage of WordPress installs in Sweden at 34 %. Out of those websites 83,785 did not disclose a version, so for this analysis, those websites has been excluded. This means there are 157,154 websites that can be used in this analysis.
The earliest version of WordPress on our list was a website with version 1.5.2. that was released on 14 August 2005. According to CVEDetails, this version has 247 vulnerabilities. Furthermore, this website is tied to a business. But this is the least updated WordPress website. What version are the majority of websites on?
Sentor analyzed 240,939 Swedish WordPress websites, and out of those websites, 83,785 did not disclose a version. Thus, we could analyze the versions of 157,154 websites. The results said that 32,981 websites were updated to the latest version. This means that 124,173 (79 %) websites were not updated to the latest version.
Showcase of the Litespeed Cache plugin
Litespeed Cache is a popular plugin for WordPress with over 3,000,000 installations. In 2021, Emil Kylander Edwartz discovered a medium severity vulnerability on this plugin. Litespeed Cache is a cache plugin, and one of the cache possibilities is for CSS code that is used to apply styling to websites. To update this cache, Litespeed Cache push content to the WordPress websites from their servers through a POST request. For security measure, the plugin only accepted these requests from a specific list of IP addresses that was controlled by Litespeed Cache. However, due to a security flaw, it was possible to make the plugin accept these requests from any origin as long as a specific HTTP header was present.
This means that it was possible to inject any arbitrary CSS content to a WordPress website that has this plugin, furthermore the CSS is stored inline on the webpages HTML. This means that it is possible to inject your own styling to a website. However, due to another vulnerability known as Cross-Site-Scripting (XSS), it was possible to inject arbitrary Javascript to the website as well. By
combining the XSS and the logic flaw, it was possible to inject your own instructions that is executed on the frontend application without being authenticated. If an authenticated administrator visits this malicious web page, it was possible to upload PHP code that will hijack the website. Another threat is using this vulnerability to phish for passwords or redirecting the website to a malicious website. WPScan gave this vulnerability CVE number CVE-2121-24964. Large companies were alerted about their systems being potentially vulnerable to this by Emil Kylander Edwartz.
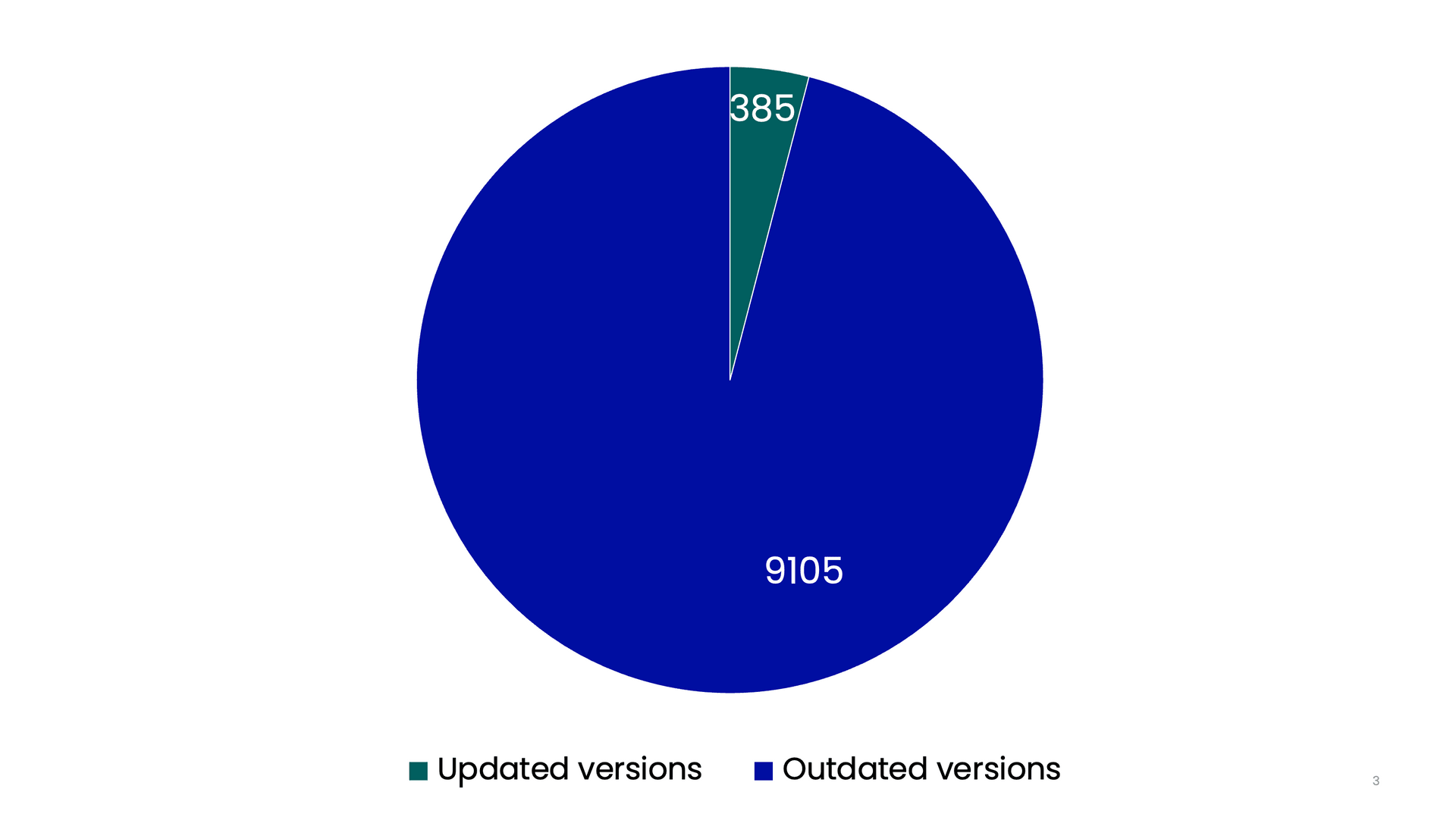
According to our records, 14,564 Swedish websites are using this plugin as of November 2023. How many websites have been updated since 2021 when this was discovered? Out of those, we gathered the versions of 9,490 WordPress websites that used Litespeed Cache. From there, 385 websites still used a vulnerable version, which puts the percentage of updated websites at 96 % after two years. Out of the vulnerable websites, one belonged to a large company. This company has now updated their website.
Amplified Brute Force
In WordPress, you can utilize XML-RPC for numerous actions. It's an interface where you can integrate with the website through another system. Logging in with a username and password using this interface is possible.
The XML-RPC login came with some unexpected issues. You could send multiple login requests in a single web request.
For one web request, you could perform 10,000 login tries. That's a million login tests in 100 web requests, thus making dictionary attacks a lot faster and more fruitful for attackers. Fortunately, WordPress mitigated this in WordPress version 4.4 and later.
Administrative privileges can lead to server access
The WordPress software has no default protection against password guessing attacks for its users. It’s essential that users implement unique and secure passwords to decrease the risk of their account being hacked. Especially if the user has an administrator role. An administrator account can also be tricked to commit administrator tasks if a session riding attack is present, utilizing for example a CSRF or an XSS vulnerability. Session riding requires no knowledge of the credentials of the victim account.
If an administrator session or credentials is compromised, the attacker can easily privilege escalate to server access if no security mechanisms are implemented, such as hardened file and WordPress permissions. This is because of WordPress rich features, such as plugin upload and theme modification. In a standalone WordPress installation, it is possible to upload a backdoored plugin that will allow the attacker to run Linux commands through PHP functions such as shell_exec, exec, system, popen, et cetera.
From this stage, the attacker could exfiltrate the database for the WordPress applications, such as the wp_users table. This table contains hashed passwords, usernames, emails, and more. Furthermore, it can be used to move laterally or vertically in the server environment, potentially causing breaches on other services on the server or network.
How do I keep my WordPress website secure?
There are a few things you can do to increase the security in your WordPress website and the possibility to mitigate potential vulnerabilities. These actions include:
1. Regularly update the WordPress core along with themes and plugins. Keep an eye out for Dependency Confusion.
2. Run WPScan against your website. WPScan shows if any sensitive files are exposed or if your site has any vulnerable dependencies.
3. Use unique and strong passwords for your accounts.
4. Enable Multi-Factor Authentication (MFA).
5. Enable a security plugin, preferably one that is from a reputable source such as Sucuri or any other well known security company.
6. Optional, turn off dangerous functions in PHP such as shell_exec, passthru, system, et cetera. A guide for how to do this can be located here.
7. Optional: turn off plugin upload and file modification from the administrators panel to prevent privilege escalation.
8. Firewall unnecessary incoming and outgoing ports on the server.
9. Use proper file permissions and ownership on the WordPress files. A guide for this can be located here.
10. Disallow PHP file execution on specific directories, for example the uploads directory.
11. Change the WordPress database prefix.
12. Disable directory indexing.
13. Disable XML-RPC if it’s not needed.
Still feel unsure about how to protect your WordPress website?
As mentioned above, keeping WordPress websites secure can be a challenging task. If you suspect that your website is vulnerable or simply just want to evaluate its security posture, feel free to contact us, and our experienced security consultants will disclose any potential vulnerabilities
Contact us
We offer several contact routes and provide feedback as soon as possible. If you have sensitive information, we ask you to use the encrypted method.
+46 8 545 333 00
We answer 24/7info@sentorsecurity.com
For general inquiriessoc@sentorsecurity.com
Use our PGP-key